Ms.different Leak
Sometimes, a little bit of information, perhaps just a tiny piece, seems to just come out into the open. It’s like when you’re trying to put together a puzzle, and then suddenly, a piece you weren't even looking for appears, fitting perfectly or, you know, at least giving you a new angle. This idea of things becoming visible, especially when they were once kept quiet, is a lot like what people talk about with a "ms.different leak." It’s about how details, maybe even some unexpected ones, find their way into public view, sparking all sorts of conversations and thoughts.
You see, there's a natural curiosity in us all, isn't there? We often wonder what's happening behind the scenes, what makes things tick, or what someone might be keeping under wraps. That kind of wondering is a bit like the feeling you get when you hear about something like a "ms.different leak." It’s not just about the information itself, but also about the questions it raises, and how it changes the way we look at things. It can feel, in some respects, like pulling back a curtain on something that was previously out of sight.
And when we talk about things coming to light, or figuring out how something truly works, it often means looking closer at the basic building blocks. Whether it’s how a piece of software operates, or how certain access is granted within a system, getting down to the simple parts can really show you the true picture. This is, actually, where the idea of understanding what’s really going on, much like the idea behind any "ms.different leak," truly begins, by just examining the foundational bits.
Table of Contents
- What's the Big Deal About ms.different leak?
- Getting Started- Peeking at Code with ms.different leak
- How Do We Find Out What's Really Going On?
- Crafting Simple Tools for a ms.different leak Investigation
- Why Do We Need Special Access for ms.different leak Details?
- Setting Up Permissions for a ms.different leak Deep Dive
- What Happens When Information About ms.different leak Gets Out?
- The Ripple Effect of a ms.different leak
What's the Big Deal About ms.different leak?
So, when people talk about a "ms.different leak," what are they really getting at? It’s not always about a grand, dramatic reveal, but more often about the gradual unfolding of information that was, for some reason, not openly available before. Think of it like someone sharing a bit of a secret, or perhaps a puzzle piece that helps everyone see a bigger picture. It could be anything from a small detail about how a system works to a broader insight into a process, and that, you know, can be quite interesting for many people.
The core idea here is that something hidden is now out in the open. This connects a lot to the kind of work people do when they want to truly understand how something operates from the inside. For instance, if you want to really see how a piece of software functions, you might use a special tool. One such tool, `radare2`, which comes with the Kali system, helps you look at the fundamental parts of a program. It lets you take something that looks like a finished product and break it down into its basic instructions, allowing you to actually see what makes it go. This process of breaking things down, to be honest, is a lot like trying to figure out the source of a "ms.different leak" – you're trying to get to the root of things.
This kind of examination, where you peek inside something to see its inner workings, helps us grasp the mechanics of how things are put together. It's a way of gaining a much deeper grasp of things, rather than just accepting them at face value. So, when information, like a "ms.different leak," comes to light, it prompts us to look at things with a fresh perspective, asking what the underlying structures or intentions might be. It’s about going beyond the surface appearance, and that, in a way, is pretty cool.
Getting Started- Peeking at Code with ms.different leak
To really get a feel for how things work, especially when we're talking about something like a "ms.different leak" where you want to see what's actually happening, it can be helpful to try it out yourself. We can, you know, start with something very simple. Imagine you have a tiny program, just a few lines of instructions. If you want to understand its true nature, you don't just run it; you take it apart. This is where a tool like `radare2` becomes very useful, as a matter of fact, because it helps you do just that.
The process involves taking that small program and, in a sense, reverse-engineering it. You look at the raw instructions that the computer understands, rather than the neat code a person might write. This act of disassembling something is about stripping away the layers to expose the fundamental commands. It’s like taking a watch apart to see the tiny gears and springs. By doing this, you can, pretty much, observe exactly what the program is doing, step by tiny step. This kind of deep look is what helps you truly "see what is really" happening inside, a lot like trying to understand the full scope of a "ms.different leak."
This method of looking at the very core of a program gives you an unfiltered view. It shows you the simple logic and actions that create the overall behavior. So, when we talk about a "ms.different leak," it often means getting access to these kinds of basic, unfiltered details that reveal the true operation of something. It's about getting past the presented version and seeing the actual mechanics, and that, you know, can be quite revealing for sure.
How Do We Find Out What's Really Going On?
So, you might be asking yourself, how do people actually figure out what’s truly happening, especially when there’s talk of something like a "ms.different leak"? It often comes down to looking at things from a different angle, getting a view that isn't the one typically presented. When we mentioned disassembling a program, that's a prime example. You’re not just accepting what the program is supposed to do; you’re looking at the actual instructions it’s given, which, you know, can be very telling.
This kind of investigation involves a bit of detective work, really. It's about taking something that seems complete and breaking it down into its constituent parts to see the individual pieces at play. When you disassemble code, you're essentially translating the computer's language back into something a human can interpret, even if it's a bit technical. This process lets you observe the flow of information, the decisions the program makes, and the actions it takes, which, in some respects, gives you a clearer picture than just seeing the final outcome.
The goal is always to get to the bottom of things, to uncover the underlying truth. This desire to "see what is really" happening is a strong motivator, particularly when information, like a "ms.different leak," suggests there's more to the story than meets the eye. It's about being able to trace the origins of an action or a piece of data, and that, for many, is a really important step in understanding any situation fully.
Crafting Simple Tools for a ms.different leak Investigation
Sometimes, to truly understand how information might surface, or how a "ms.different leak" could happen, you need to think about how simple actions can have big effects. Remember, the original text talks about creating a "fairly simple hacking bat file" using just Notepad. This isn't about doing anything overly complicated; it's about seeing how basic commands, put together in a specific order, can make a computer do something. You just open a simple text editor, like Notepad, and type in some instructions. It's, you know, pretty straightforward.
The beauty of this approach is its simplicity. You don't need fancy software or extensive training to begin exploring how basic computer commands work. By simply typing lines of text into Notepad and saving it with a specific file type, you create a small set of instructions that the computer can follow. This kind of basic scripting is, in a way, a foundational step for anyone interested in how systems respond to commands, and it shows that even small, simple files can initiate actions that might, you know, lead to interesting outcomes.
This idea of creating something simple to achieve a particular result can be applied to many situations, including understanding how information, perhaps like a "ms.different leak," might spread or be revealed. It highlights that sometimes, the most straightforward methods can be quite effective in getting a system to perform a task, or in revealing how certain processes are initiated. It's about understanding the cause and effect at a very basic level, which, you know, is a very useful skill to have when trying to piece together any kind of puzzle.
Why Do We Need Special Access for ms.different leak Details?
Have you ever tried to open a door that was locked, or access a file on a computer that said "permission denied"? It's a common experience, and it points to a very important concept: control over information and system functions. This idea of needing special permission is, you know, particularly relevant when we consider something like a "ms.different leak." Why would some details require higher levels of access to view or even understand?
The original text mentions configuring "sudo privileges for our new user" using the `visudo` command. This is about giving a user the ability to perform tasks that are usually reserved for system administrators – the people who have the keys to everything. Without these elevated permissions, certain actions simply can't be carried out, and certain files or settings can't be changed. It’s a way of keeping things secure and making sure only authorized people can make big changes, and that, you know, is pretty important for system stability.
So, when we think about information, especially sensitive information that might be part of a "ms.different leak," the concept of access becomes very important. Some details are just not meant for everyone to see, or to be altered by just anyone. This control mechanism is put in place to protect systems and data. Understanding how these permissions work, and how they are granted or restricted, is a key part of understanding how information flows, and how something that was once protected might, you know, become available to a wider audience.
Setting Up Permissions for a ms.different leak Deep Dive
When you want to really get into the nuts and bolts of a system, especially if you're looking for details that might be related to a "ms.different leak," you often find that you hit a wall if you don't have the right keys. The `visudo` command, mentioned in the original text, is a very specific way of granting those keys. It's not just about typing a command; it's about carefully editing a file that controls who can do what on a system. This kind of careful setup is, you know, a very important step.
This process of setting up "sudo privileges" is a bit like giving someone a special pass that lets them into restricted areas. It means they can run commands that normally only the system's main administrator could run. This level of control is put in place to ensure that only trusted individuals can make significant changes or access sensitive parts of the system. It’s a foundational part of keeping things safe and in order, and that, to be honest, is a pretty big deal.
Understanding how these permissions are managed gives us insight into how information is protected, and how, perhaps, a "ms.different leak" might occur if those protections are somehow bypassed or misconfigured. It highlights that gaining access, or having information become accessible, often involves specific actions related to system privileges. It's about recognizing that some doors are meant to stay shut, unless, you know, you have the right kind of permission to open them.
What Happens When Information About ms.different leak Gets Out?
When information, like a "ms.different leak," makes its way out into the open, it's not just about the data itself; it's about the changes that follow. Think back to disassembling a program: once you see what's really inside, you can't unsee it. The way you understand that program, or even the way you use it, might shift. Similarly, when details that were once private become public, they can, you know, change how people perceive a situation, a company, or even an individual.
This sudden transparency can lead to all sorts of discussions and new perspectives. It’s like a light being shone on something that was previously in shadow. People start asking questions, connecting dots they couldn't see before, and forming new opinions based on the newly available information. This process of re-evaluation is, actually, a natural human response to new facts, especially when those facts were, in some respects, not meant for public consumption.
So, the act of information becoming known, particularly through something like a "ms.different leak," often leads to a recalculation of sorts. It can prompt organizations to review their practices, or individuals to reconsider their views. It’s a dynamic process where the release of information sets off a chain reaction of analysis and discussion, and that, you know, can have pretty wide-ranging effects.
The Ripple Effect of a ms.different leak
The moment information, particularly something like a "ms.different leak," becomes public, it doesn't just sit there. It starts a chain of events, much like a stone dropped into a calm pond creates expanding circles. The initial piece of information, perhaps something uncovered by looking at a program's core or through a simple script, can lead to further questions and investigations. It’s a bit like when you find one clue, and that clue, you know, points you to another, and then another.
This spreading impact means that the initial "ms.different leak" can prompt a closer look at related systems, policies, or even people. If, for instance, the leak revealed something about how a program handles data, it might make people question the security of other programs. Or if it showed how certain privileges were used, it might lead to a review of access controls across an entire network. This kind of expanded scrutiny is,
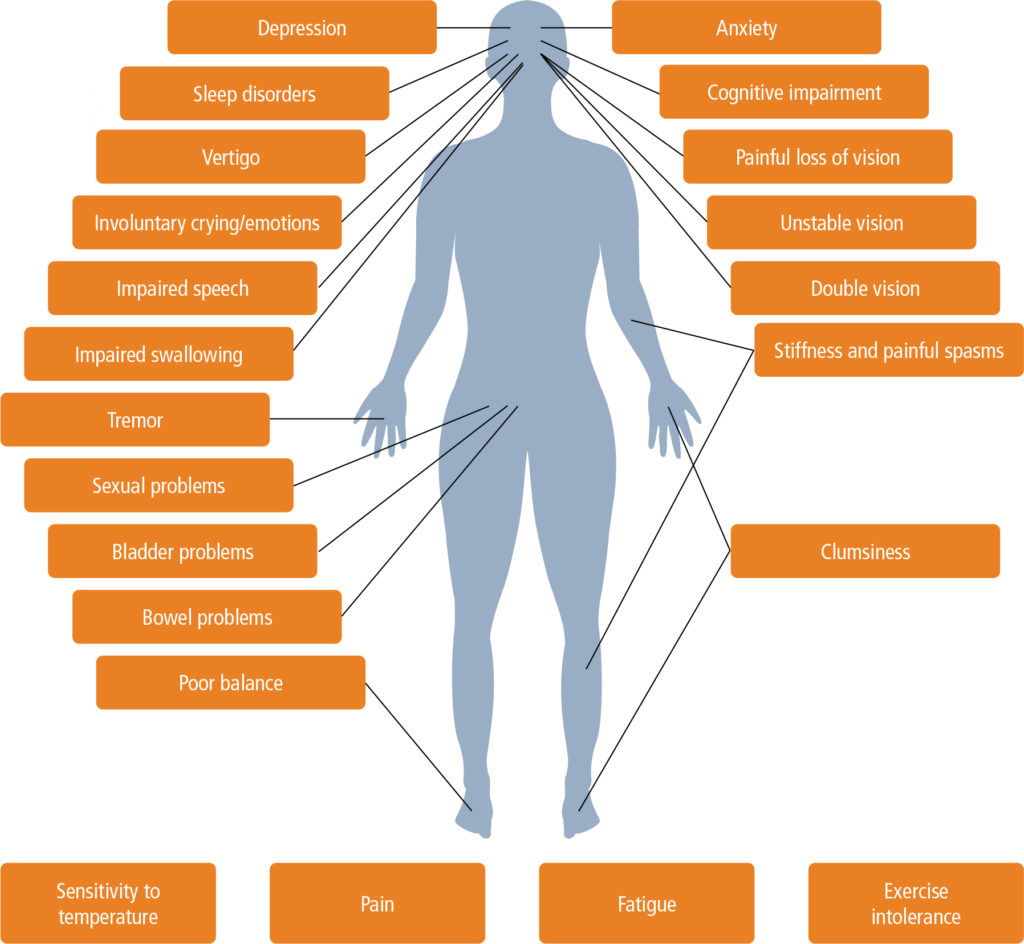
Multiple sclerosis in primary care – diagnosis and early treatment
:max_bytes(150000):strip_icc()/weird-ms-symptoms-and-phenomena-julies-list-2440790_v2-77d3f7200923456480500fd830750433.png)
Ashwagandha Benefits For Multiple Sclerosis / 8 Science Backed Benefits
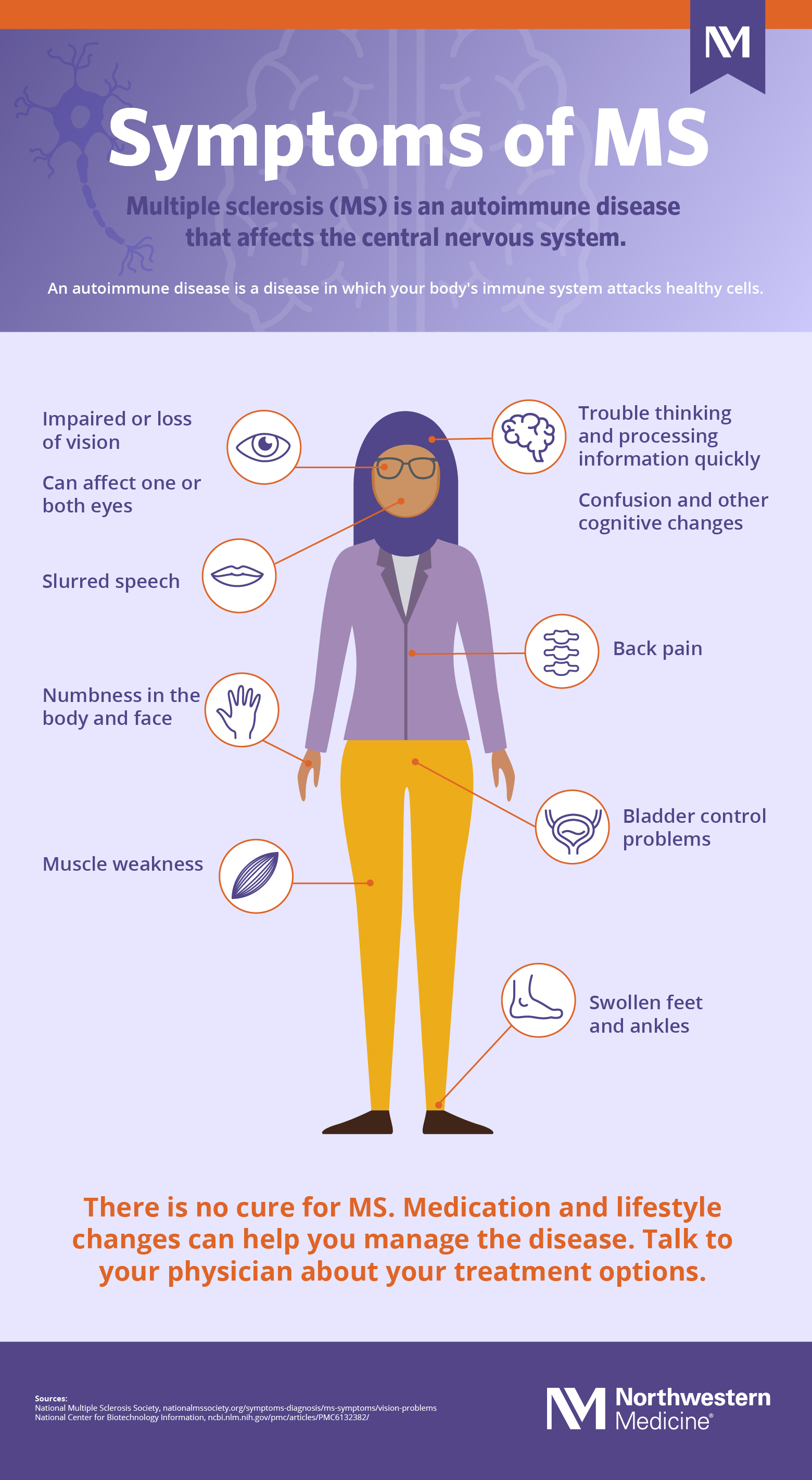
Multiple Sclerosis